Mastering the Art of Penetration Testing:
Unveiling Digital Security Vulnerabilities
Introduction: Welcome to our educational blog dedicated to the exciting world of penetration testing! In this digital era, where data breaches and cyber threats are rampant, the role of a penetration tester has become increasingly crucial. This blog aims to demystify the concept of penetration testing, equip you with the necessary knowledge and skills, and provide insights into the fascinating realm of cybersecurity.
What is Penetration Testing?
Definition and purpose of penetration testing
Different types of penetration tests (black box, white box, gray box)
Legal and ethical considerations
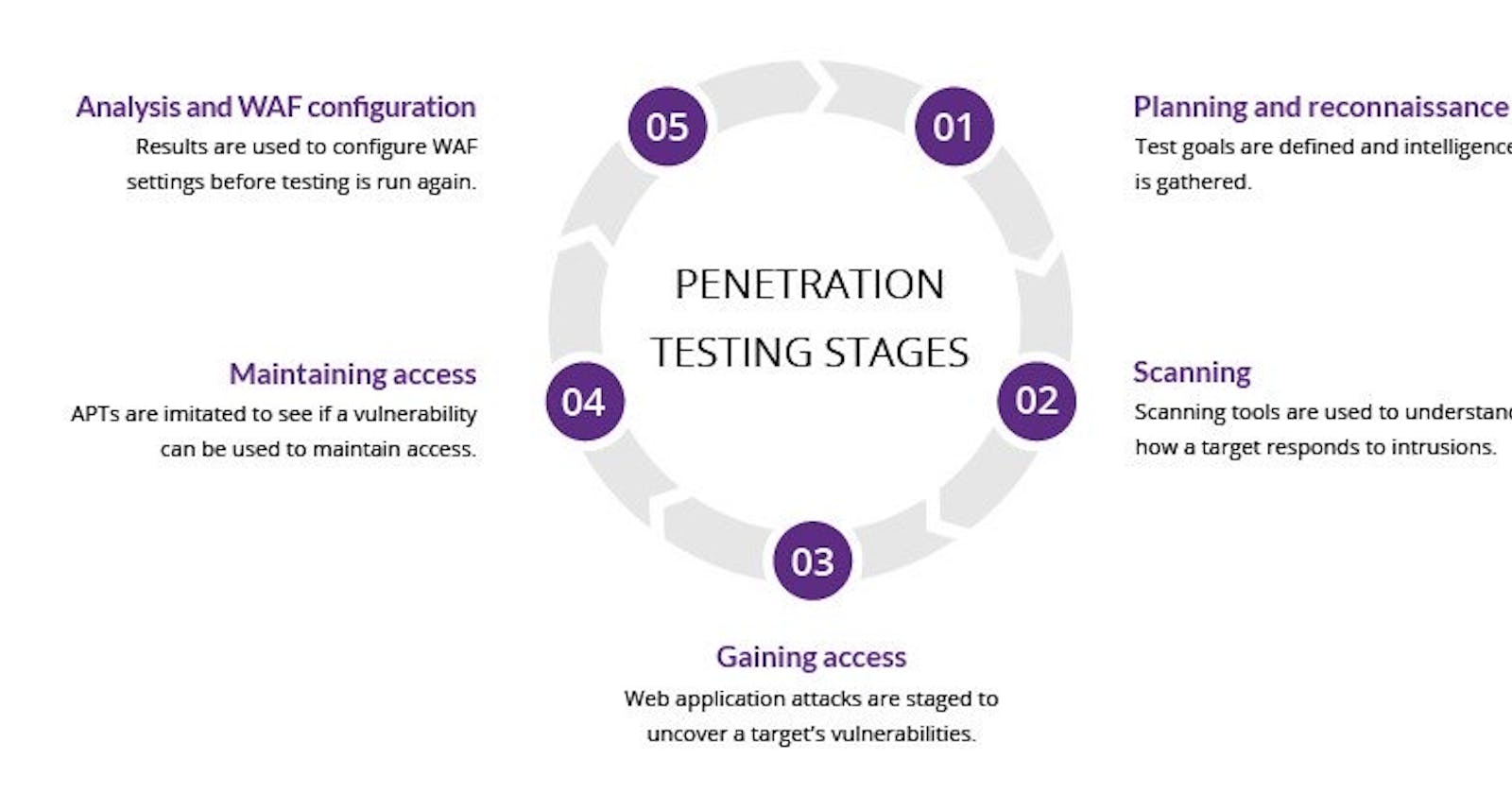
The Penetration Testing Process:
Planning and scoping a penetration test
Gathering intelligence and reconnaissance techniques
Vulnerability assessment and identification
Exploitation and gaining access
Post-exploitation and reporting
Penetration Testing Methodologies:
Overview of popular methodologies (OSSTMM, PTES, NIST SP 800-115)
Steps involved in each methodology
Selecting the right methodology for specific scenarios
Network Penetration Testing:
Scanning and enumeration techniques
Exploiting network vulnerabilities (weak passwords, misconfigurations)
Mitigating common network attacks (DDoS, MITM)
Web Application Penetration Testing:
Understanding the web application architecture
Identifying common vulnerabilities (SQL injection, XSS, CSRF)
Web application firewall (WAF) evasion techniques
Wireless Penetration Testing:
Wireless network security protocols (WEP, WPA, WPA2)
Cracking wireless encryption (WPS attacks, brute-forcing)
Securing wireless networks (WPA3, MAC filtering)
Social Engineering:
Psychological tactics and manipulation techniques
Phishing, spear phishing, and pretexting
Defense mechanisms against social engineering attacks
Penetration Testing Tools:
Popular tools for reconnaissance, scanning, and exploitation
Automated vs. manual testing approaches
Building your own penetration testing toolkit
Advanced Penetration Testing Techniques:
Evading detection and staying stealthy
Exploiting zero-day vulnerabilities
Red teaming and simulated real-world attacks
Penetration Testing Certifications and Career Path:
Industry-recognized certifications (CEH, OSCP, CISSP)
Developing a career in penetration testing
Continuous learning and staying up-to-date with emerging threats
Conclusion: Congratulations on completing this educational journey through the world of penetration testing! By now, you should have a solid foundation of knowledge and practical skills to embark on a career in this exciting field. Remember, with great power comes great responsibility. Always adhere to ethical guidelines and use your expertise to enhance the security posture of organizations in an ever-evolving digital landscape. Stay curious, keep learning, and enjoy the fulfilling journey of being a penetration tester.
Disclaimer: This blog is intended for educational purposes only. Always seek proper authorization before conducting any penetration testing activities and ensure compliance with legal and ethical guidelines in your jurisdiction